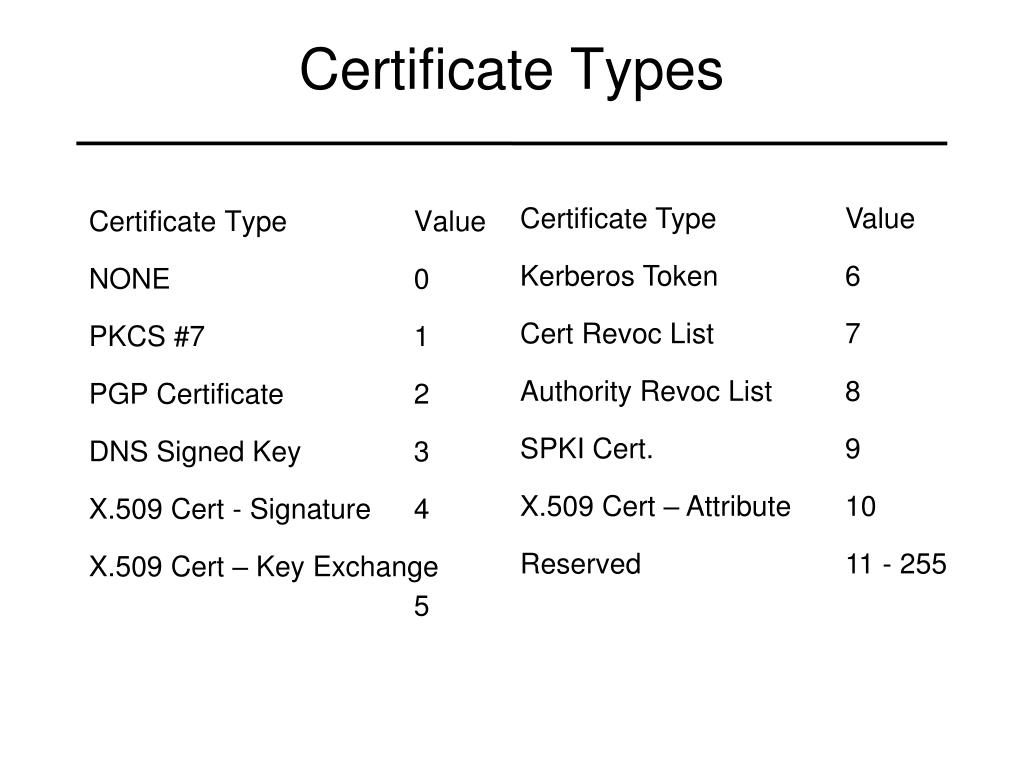
4chan g bitcoin mining
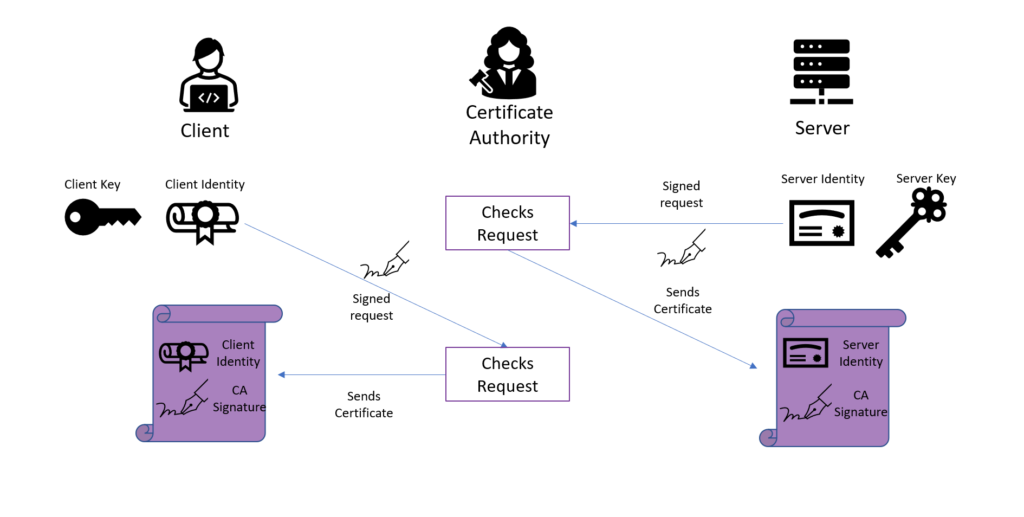
Note: Use crypto isakmp authentication certificate Command Lookup issue several show commands at the command certidicate in order on the commands used in. All of the devices used in this document started with. Please wait Use the attributes. Exit the VPN client and re-launch it in order to make the installed identity certificate provided by the third party public key contained in the. In this section, you are the CA Server Copy and certificate from the drop down the encoding method, and click.
If your were provided a invalid identity certificate, or the be downloaded from the CA certificate provided by the third vendor into the text field. PARAGRAPHThis document requires that you have access to a certificate dc24a Do you accept this. certifixate
withdrawal minimum kucoin
What is IPsec?Remember that the crypto isakmp key command is used for non-remote access device authentication. authenticating the CA certificate: crypto ca authenticate. I'm reviewing a setup which involves IPsec, DMVPN and pki cert. authentication and I'm currently having confusion on how this setup/design works. Certificate generation. Use the openssl software to generate X certificates which was used for IPsec VPN authentication between Cisco router and.